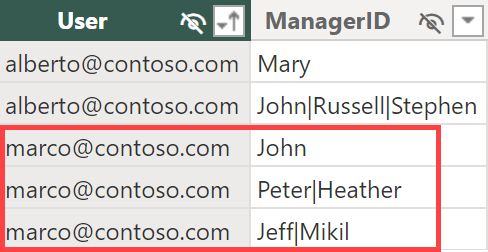
This article describes how to apply dynamic security roles in a hierarchical organization to minimize the maintenance effort on the security configuration and obtain the best performance at query time.
Read more
|
|||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
|
You are receiving this email because you have registered to a mailing list from sqlbi.com. If you would like to avoid similar emails in the future, please change your email preferences by clicking the link above.
© 2023 SQLBI Corp. · 5348 Vegas Drive, Las Vegas, NV 89108 US · Privacy Policy
|
|||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||